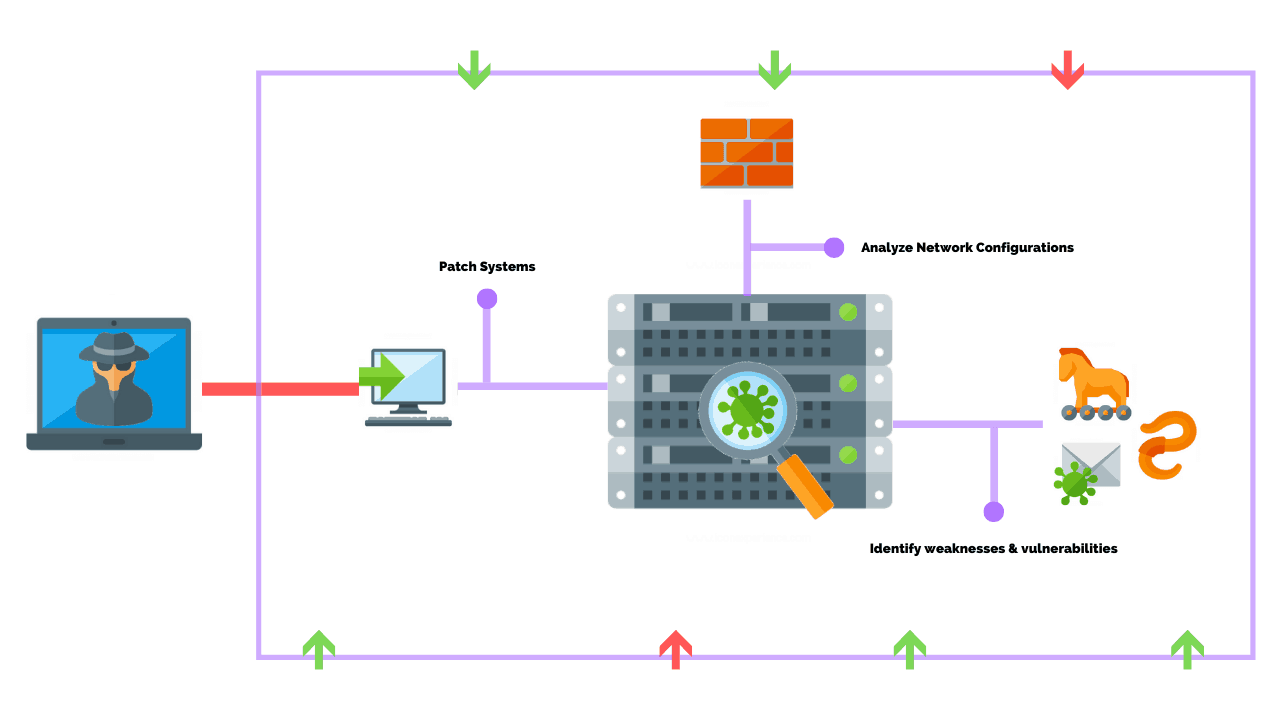
Penetration test Exploit Network security Vulnerability, others, text, information Technology, business png | PNGWing
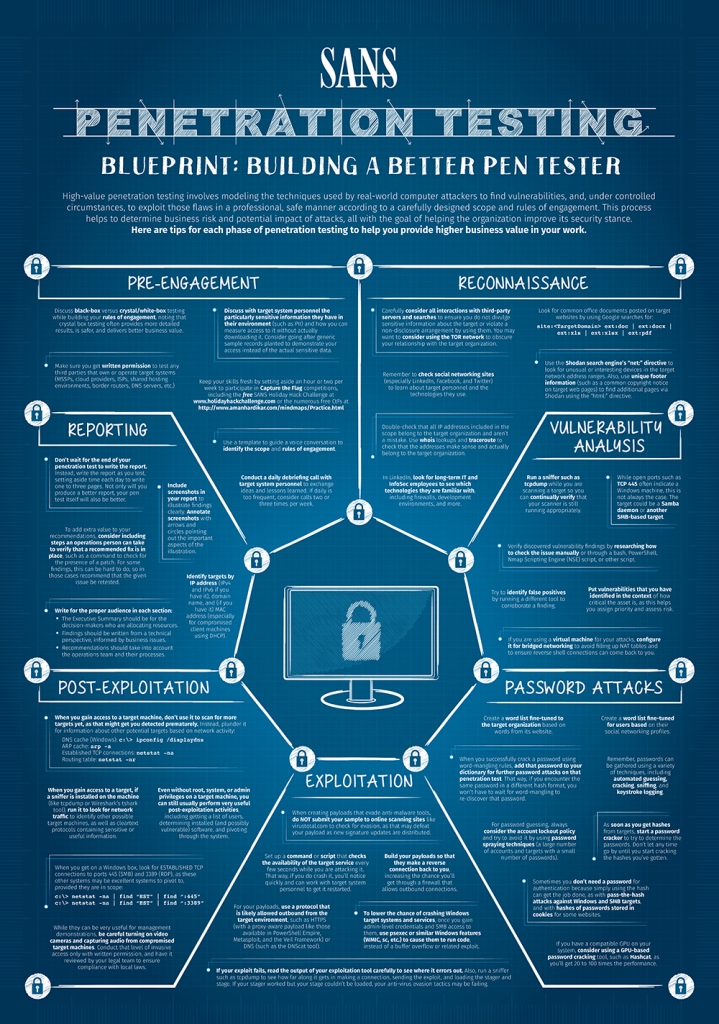
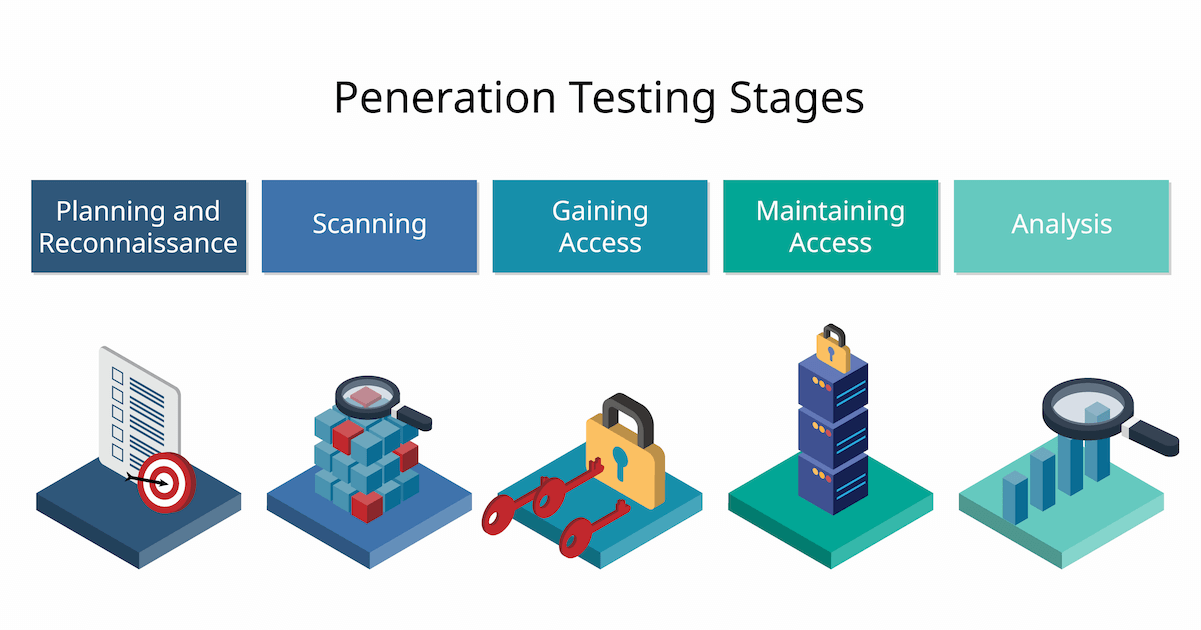
SANS Penetration Testing | SANS Poster: Building a Better Pen Tester - PDF Download | SANS Institute

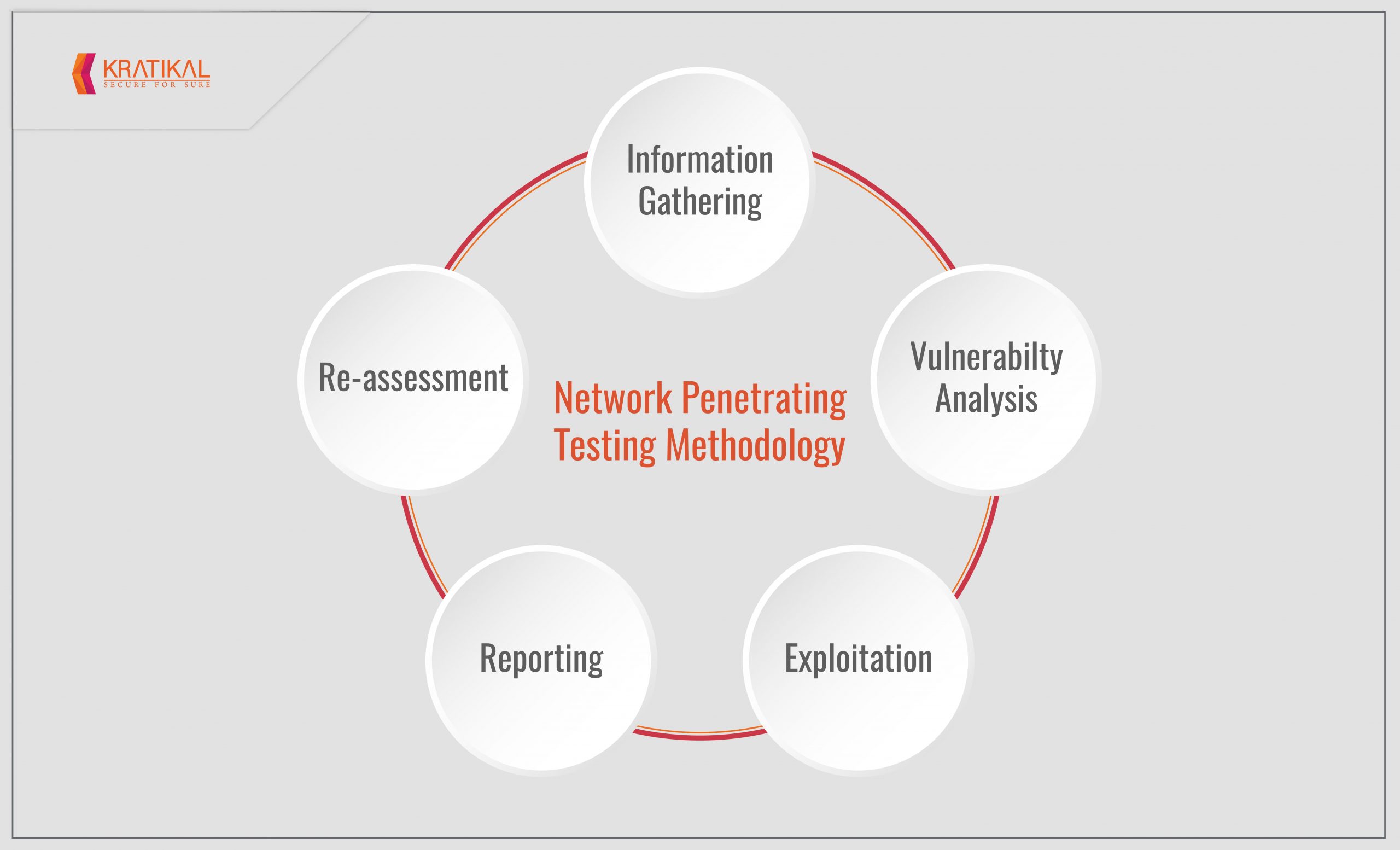
Emad Shanab - أبو عبد الله on Twitter: "Network Penetration Testing, Methodology,Guide,Tutorials and Checklists:- https://t.co/97rJgllByv https://t.co/c7Mhy7l5O4 https://t.co/xaMuq91Dfd https://t.co/uKnabHfUOx https://t.co/2cTLzSY1zk https://t.co ...

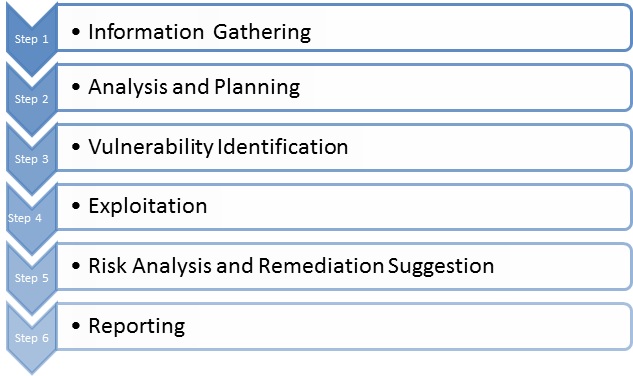
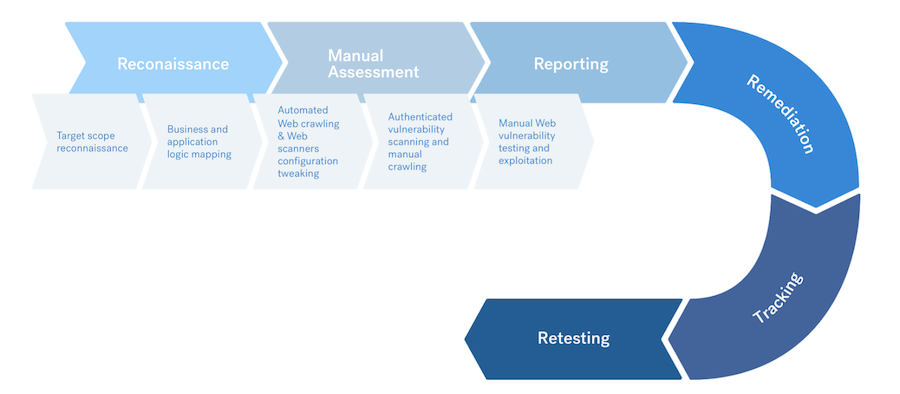
Penetration Testing Methodology All the necessary documents for the... | Download Scientific Diagram
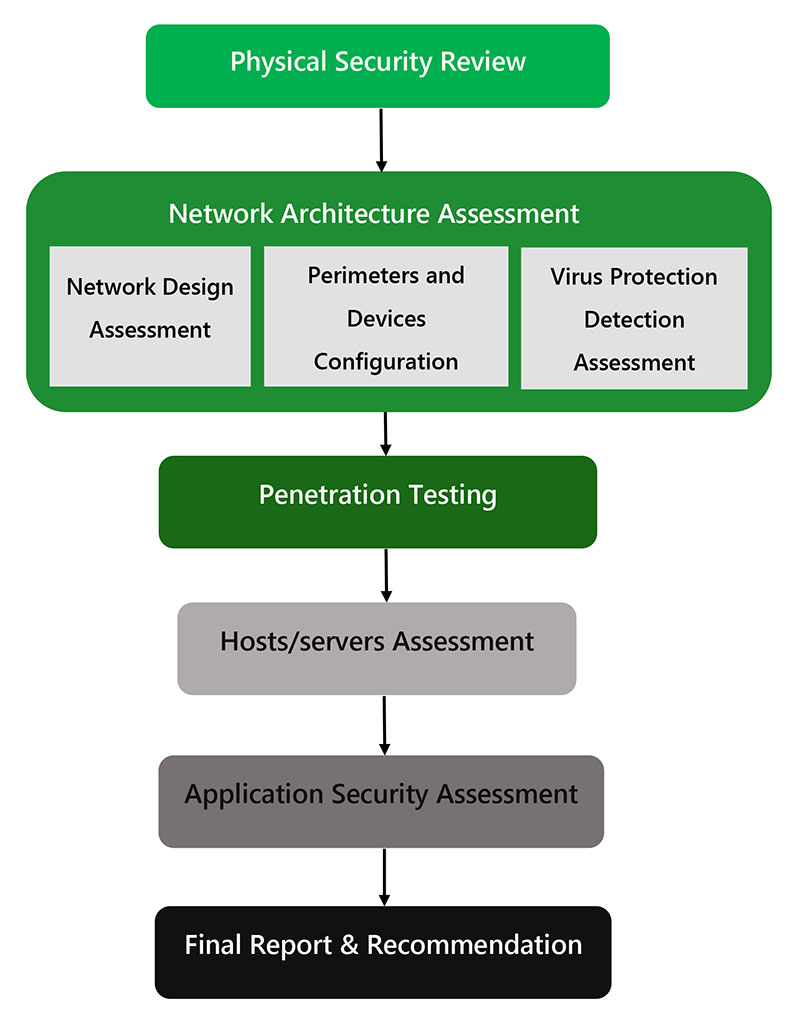
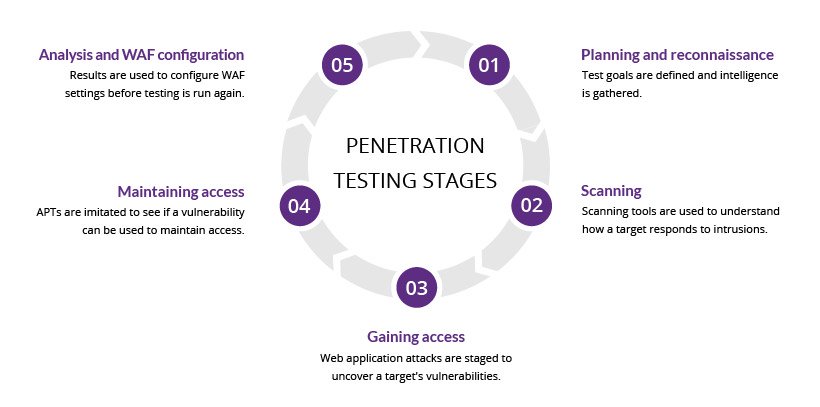
![PDF] Network Security Assessment Using Internal Network Penetration Testing Methodology | Semantic Scholar PDF] Network Security Assessment Using Internal Network Penetration Testing Methodology | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/df619a87b5b76881877835a48e7042c4610b94df/2-Figure2-1.png)